New paper on Just-in-time Code Analysis
Eric | May 19, 2017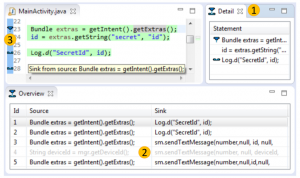 In a collaborative effort with Karim Ali (University of Alberta), Ben Livshits (Imperial College London), Justin Smith and Emerson Murphy-Hill (North Caroline State University), my Ph.D. student Lisa Nguyen and myself have just concluded a new piece of research on Just-in-time (JIT) static code analysis. The approach, which we exemplify with a JIT taint analysis for Android, can be applied to most static analyses
In a collaborative effort with Karim Ali (University of Alberta), Ben Livshits (Imperial College London), Justin Smith and Emerson Murphy-Hill (North Caroline State University), my Ph.D. student Lisa Nguyen and myself have just concluded a new piece of research on Just-in-time (JIT) static code analysis. The approach, which we exemplify with a JIT taint analysis for Android, can be applied to most static analyses 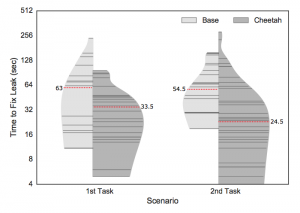 and allows those analyses to execute more efficiently in integrated development environments. In particular, the analysis is tuned such that it executes first in code recently edited by the programmer and then searches its way further “outward” from there. As our experiments indicate, this decreases round-trip times for programmers and hence increases their productivity during the fixing of security vulnerabilities.
and allows those analyses to execute more efficiently in integrated development environments. In particular, the analysis is tuned such that it executes first in code recently edited by the programmer and then searches its way further “outward” from there. As our experiments indicate, this decreases round-trip times for programmers and hence increases their productivity during the fixing of security vulnerabilities.
A preprint of the work, accepted for publication at ISSTA, is now available online, as is our implementation and data set:
Just-in-Time Static Analysis (Lisa Nguyen Quang Do, Karim Ali, Benjamin Livshits, Eric Bodden, Justin Smith, Emerson Murphy-Hill), In International Symposium on Software Testing and Analysis (ISSTA), 2017. (To appear.)
Cross-posted from Secure Software Engineering





