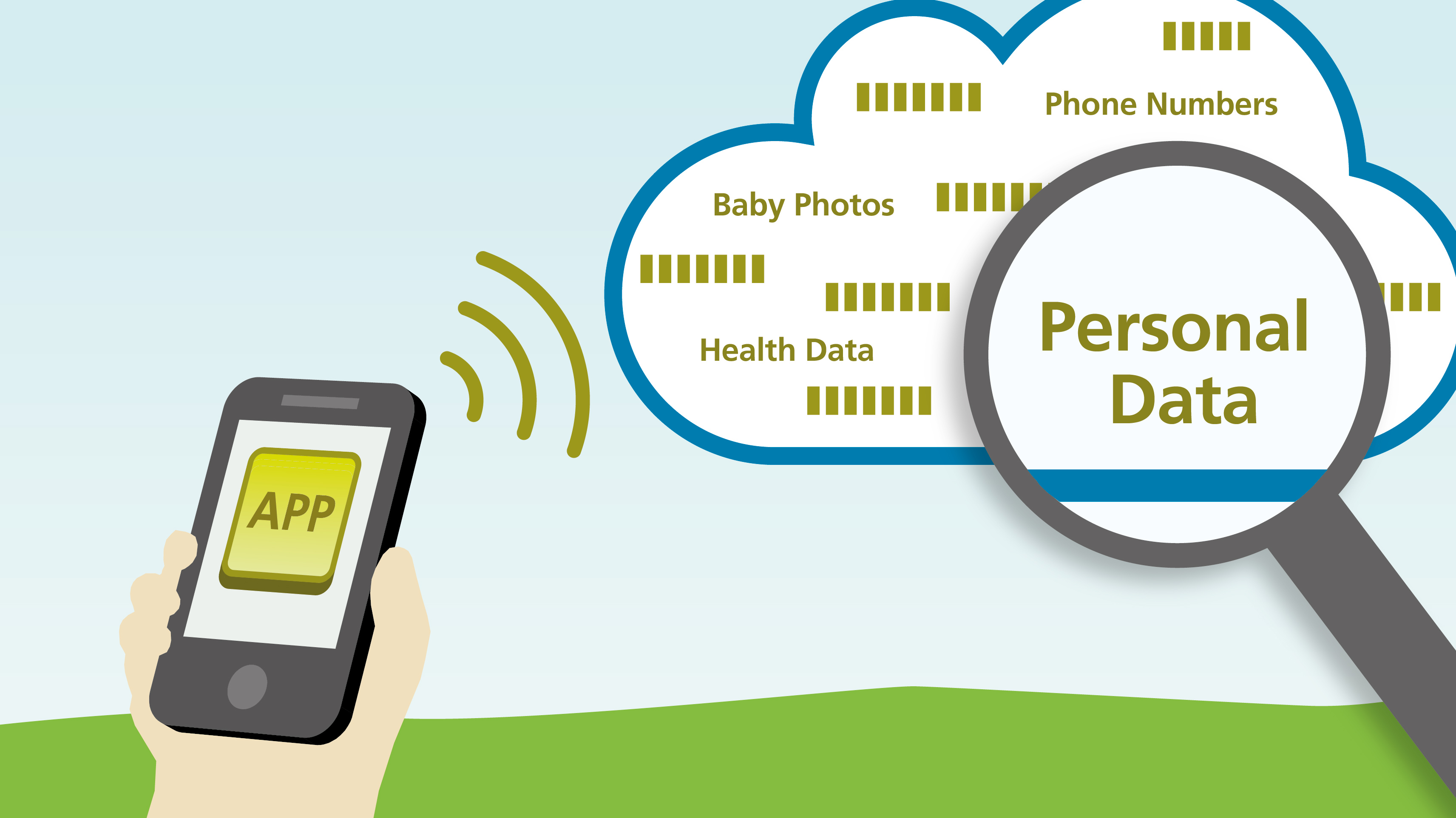
With the help of CodeInspect, Appicaptor and an internally developed tool, researchers from TU Darmstadt and Fraunhofer SIT have found that many mobile applications store private information in the cloud, in an easily accessible manner.
Many users of mobile applications want their data to be synced across multiple platforms (iOS/Android/Windows/OSX/…). For app developers it is typically hard to support synchronization, as they need to set up backend servers on which the data can be stored and synchronized. Cloud providers such as Amazon and Parse.com therefore provide backends as a service (BaaS). With BaaS, app developers can simply connect to pre-configured servers using a few lines of program code. This makes data storage and synchronization through the cloud very easy. Some apps use BaaS to share public data, which is ok as long as the data is configured to be read-only. Many apps, however, use BaaS also to store confidential data such as user names, email addresses, contact information, passwords and other secrets, photos and generally any kind of data one can think of. Such data should only be accessible to the individual app user who stored the data. The researchers found more than 56 million sets of unprotected data, including email addresses, passwords, health records and other sensitive information of app users, which may be easily stolen and often manipulated. Read the official release here.
Cross-posted from SEEBlog
 The
The