UPDATE: THE POSITION HAS BEEN FILLED!
Is this for you?
The following code uses the symmetric encryption scheme AES, for instance to store some application data encrypted on disk. The code contains at least four different severe API-usage mistakes that may cause the code to crash or to be insecure:
String secretKey = "x$&78_;:$%$ä0$%=$%4352";
byte[] keyBytes = secretKey.getBytes();
SecretKeySpec secretKeySpec = new SecretKeySpec(keyBytes, "AES");
Cipher cipher = Cipher.getInstance("AES");
Can you spot these mistakes? The more you can find, and the more you enjoy finding them, the more likely the position might be the right one for you.
The CROSSING Collaborative Research Center
The Secure Software Engineering Group is currently looking for a Research Assistant in the area of static code analysis and code generation. The position is for a doctoral researcher within the new collaborative research center CROSSING which will commence operation at TU Darmstadt in October in which the researcher will interact with many researchers from IT-Security, mostly with a focus on cryptography. Collaborative Research Centers are institutions funded by the German Research Foundation (DFG) and are established at universities to pursue a scientifically ambitious, complex, long‐term research program. The goal of the center CROSSING is to provide cryptography-based security solutions enabling trust in new and next generation computing environments. In the center researchers from different areas such as cryptography, IT security, computing hardware, quantum physics, and software engineering will collaborate. The available doctoral positions are distributed over the aforementioned areas, and will be affiliated with the research training school of the center.
Project Secure Integration of Cryptographic Software
As part of its research program CROSSING will develop an open-source software called OpenCCE which will allow users to deploy the developed solutions in a secure and easy way. This particular position is one of three within project E1 – Secure Integration of Cryptographic Software, which will coordinate, among other things, the development of OpenCCE:
Cryptography-based security solutions and cryptographic primitives/algorithms can only support trust if sound implementations exist and users and developers are supported in integrating them into their applications. Thus, the goal of this project area is to develop methods and technologies that allow for secure implementation of cryptography and enable users and developers who may not be cryptography experts in properly applying cryptography.
Software engineers are regularly overwhelmed by the usage constraints that cryptographic components impose on their application interfaces. Frequently, components are initialized incorrectly, or security-sensitive error situations remain unhandled. Furthermore, programmers may disregard composition rules, leading to insecure combinations of cryptographic components. This project addresses these issues by providing an integrated system that not only pre-selects sensible combinations of components according to the developer’s security demands, but also helps the developer to securely integrate them into his software system.
Collaboration within the center and outside
CROSSING is associated with CASED, one of the largest and most prominent IT security research centers in Europe. In CASED, more the 250 researchers work on topics related to IT security in all different kinds of flavors. Collaboration within the center is encouraged. The position is situated within the Secure Software Engineering Group, which is also well known for a number of fruitful collaborations in Germany and abroad. The group collaborates with top universities and research organizations as well as with Fortune 500 companies such as Microsoft, Google, IBM, SAP, Software AG and Bayer AG. Engaging in such collaborations is not required but encouraged and internships at some of our partners are possible for the successful applicant.
Required skills
Applicants should have a strong desire to perform interdisciplinary research. The researcher will become part project E1, which plays a central role in the new center, and will coordinate the integration of more than a dozen cryptographic system into a joint, Eclipse-based toolbox called OpenCCE. Applicants should thus possess strong communication skills. Previous experience with developing Eclipse extensions and with static code analysis are a plus. The research focus will between the areas of static code analysis, code generation and software variability. This is a full position, payed according to pay scale E13.
TU Darmstadt has a large interest in increasing the number of female researchers, and hence particularly encourages female candidates to apply. Applicants with a degree of disability of 50% or more will be preferred in case they are otherwise equally qualified to the other candidates. It is generally possible to work part time.
How to Apply
Applicants should upload their applications on the submission form, selecting project E1, including the usual documents and indicating the applicant’s area of interest. Applications will be considered until the positions are filled. Applications by email will be rejected.
In your application you must name and describe, on the first page of your PDF document, at least three mistakes contained in the code fragment named on the top of this posting. Also describe what a correct usage of the API would look like, for the purpose of storing data encrypted on disk.
Cross-posted from SEEBlog
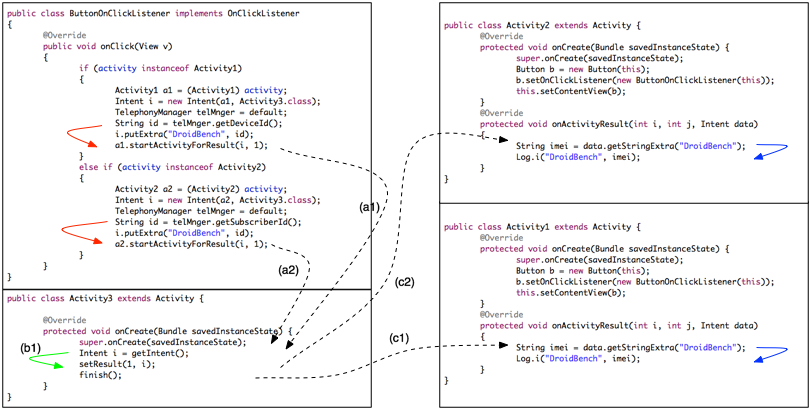

 Our taint-analysis framework
Our taint-analysis framework 




